Security Review - a Module for Drupal
When working on a project, there are many ways to increase the security of a website. One of them is the use of automated security tests that assist developers in eliminating as many security bugs as possible.
At Droptica, our Drupal developers focus on delivering the safest solutions. The Drupal CMS itself helps us in this, as it is safer than other CMSs. Thanks to the huge community focused on opensource projects, one of which is Drupal, clients, on the one hand, receive effective solutions, and on the other hand, can be sure about their security. At this point, it is worth to mention a special team dedicated to this issue, which is the Drupal Security Team.
In this text, I would like to introduce you to the operation of one of the tools to increase the security of your website – the Security Review module.
Dates
The module was released on 4 November 2009, and the most recent update was introduced on 4 October 2019. The module has a version for Drupal 7 and 8
The module’s popularity
According to drupal.org, 30,000 websites are using the module, 28,000 of which are Drupal 7 and 2,000 are Drupal 8.
Module’s creators
The module’s creator is the user named greggles. The module is supported and developed by the Acquia, CARD.com and Google Summer of Code organisations. The most commits were provided by the users coltrane (111), banviktor (58) and greggles (8).
What is the module used for?
The module performs an automatic website audit detailing many attack vectors that can lead to security errors. Here is the list of some of them:
File permissions
Saving files to the server’s root directory is dangerous and may lead to a remote code execution error. An attacker can use this vulnerability to take control of a website. More information on the correct configuration of permissions can be found at this link.
The list of tags accepted by the text formats available in the CMS
Some HTML tags are considered unsafe. This means that they may allow an attacker to take control of a website. Drupal has an HTML filtering engine that removes malicious tags - this test checks if the filtering is set up correctly.
Error reporting
Drupal may disclose information about errors to unauthorized persons. An attacker can use this information to refine an attack or find more vectors.
Unsafe file extensions
Some extensions are considered unsafe. This means that they can cause security errors such as remote code execution. This allows an attacker to take control of a website, and Security Review checks whether Drupal enables the transfer of files with unsafe extensions.
Database errors
Many database errors triggered by a single IP address are a sign that someone is trying to make a SQL injection attack. The module informs if multiple database errors were triggered from the same IP address.
Login panel brute force
Multiple failed login attempts are an indication that someone is trying to get into another user’s account. You are being informed about it.
Trusted hosts (HTTP host header attack)
Correct configuration of Trusted Host protects against HTTP host header attack, a detailed description of the settings is available at this link.
Views access
Security Review recommends that access to Drupal views should have at least minimal ‘access content’ control. This test checks whether the views have at least a minimum level of access control.
Security Review does not introduce any security fixes but only suggests where vectors of attack may be present. These are suggested changes that need to be analysed by a specialist.
Unboxing
The module installation is standard, but we suggest using the Composer:
composer require drupal/security_review
Settings
Under the address
/admin/config/security-review
you can configure the module by selecting roles that are not trusted. Security Review uses this as a basis for checking whether the users with not trusted roles have permissions to the functionalities that may cause security errors. You can also choose which items from the checklist you want to omit and choose the method of checking the trusted hosts.
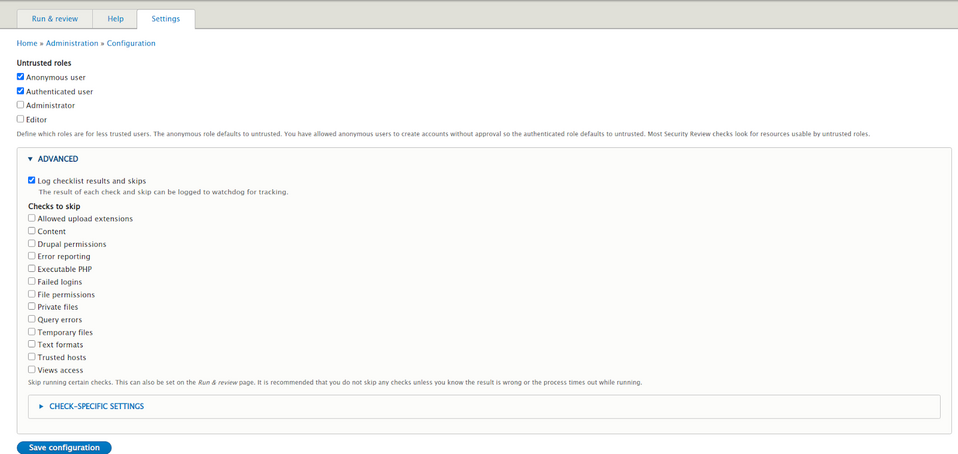
Role configuration
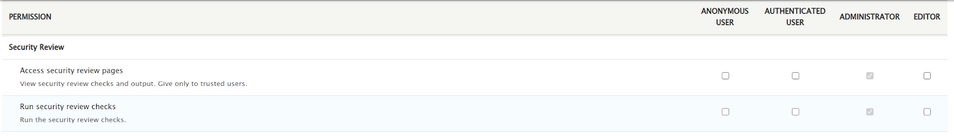
The module provides two types of permissions: ‘access security review list’, ‘run security checks’. First, you need to configure the trusted roles that will be able to read reports and run the scan. In order to do this, go to
/admin/people/permissions
and configure the permissions for selected roles:
Module’s use
The module has already been configured. To run an audit, just go to
/admin/reports/security-review
and click “Run checklist”, and Security Review will conduct the audit. You can also use the drush command:
drush secrev
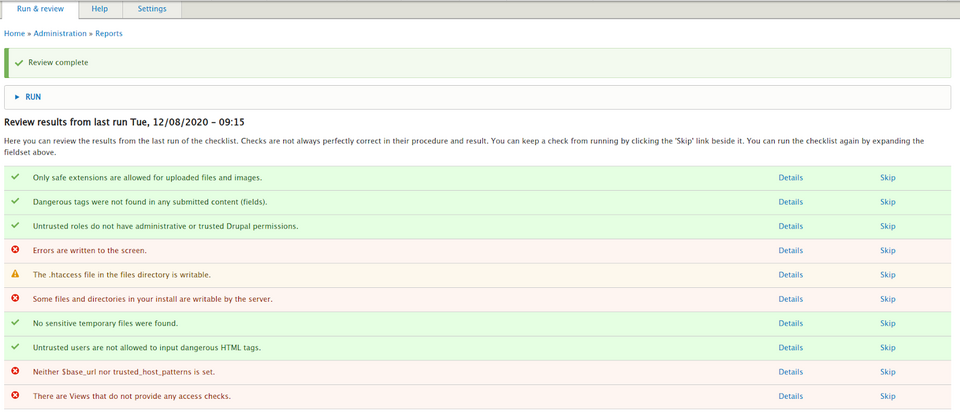
Every test has a summary that you can see by clicking on the “details”. An example for “Errors are written to the screen”:
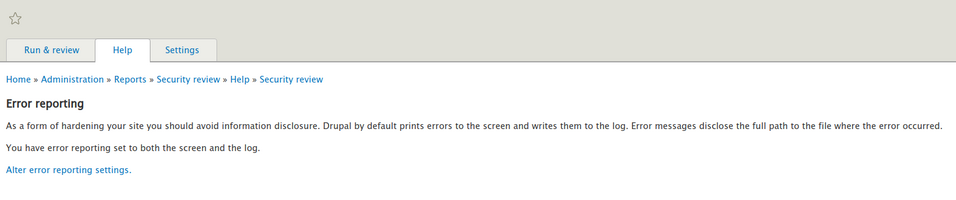
Moving on to the error logging settings, you can see that Drupal shows all the information, including the backtrace:
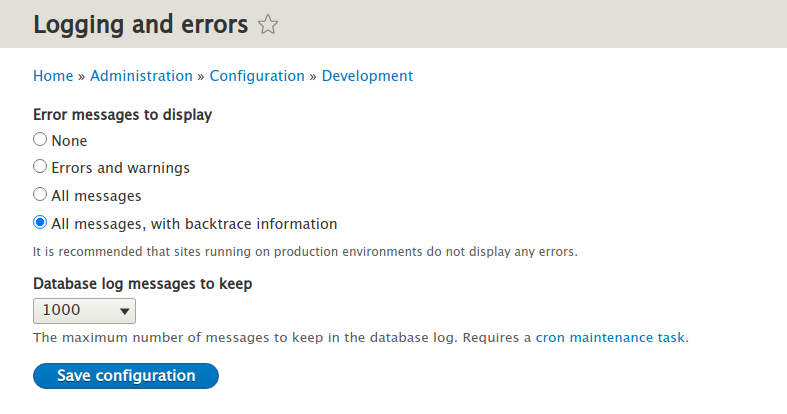
In the case of a production version of a website, set this option to “none” in order to minimise the risk of disclosing information that could help an attacker to hijack the website.
Similar information is provided for each of the security errors detected during the audit. All items should be reviewed manually, and appropriate changes should be made – if required.
Alternative modules
The Paranoia module identifies all the areas where a user may be able to trigger the custom PHP code and tries to block them. This reduces the possibility of a remote code execution error occurring. In addition, the module protects the main admin account (account with id 1), preventing its editing and blocking the possibility of uninstalling itself using the standard way (to uninstall the paranoia module, you need to edit the database manually). All the functionalities provided by the Paranoia module are intended to increase the security of a website.
Summary
The Security Review module is an extremely important and useful tool. Thanks to the information collected by the module, you gain invaluable knowledge of what should be done in order to improve the security of your website. After analysing the results, you can eliminate some of the attack vectors. Our team recommends using this module when creating a website.